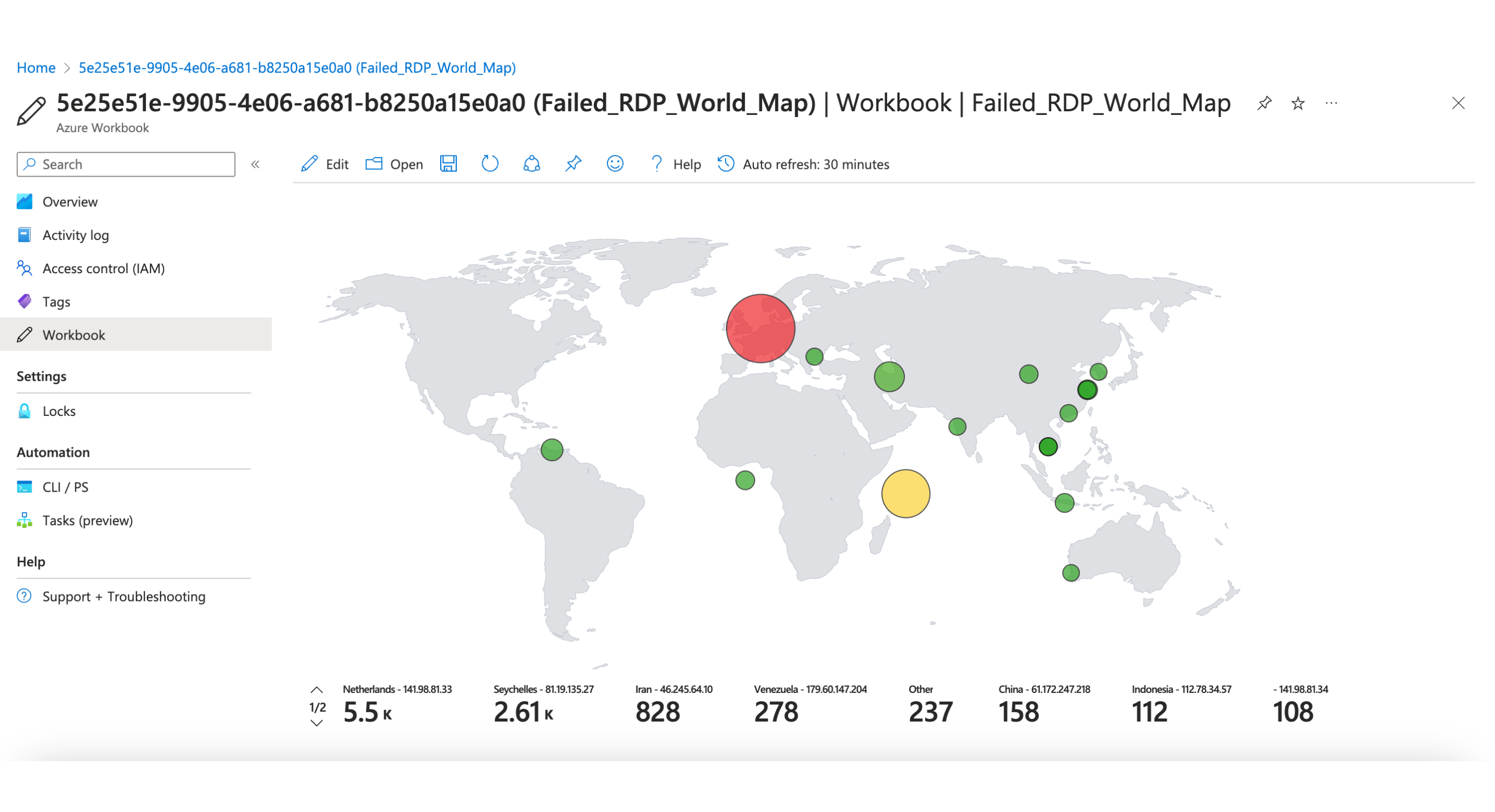
Overview
- Used custom PowerShell script to extract metadata from Windows Event Viewer to be forwarded to third-party API to derive geolocation data
- Configured Log Analytics Workspace in Azure to ingest custom logs containing geographic information (latitude, longitude, state/province, and country)
- Created Custom Fields in Log Analytics Workspace with the intent of mapping geo data in Azure Sentinel
- Built Azure Sentinel (Microsoft’s cloud SIEM) workbook to display global attack data (RDP brute force) on a world map according to physical location and magnitude of attacks